Pcap Sniffer
When working with networks, seeing what’s really happening on the wire is essential, whether you're diagnosing an issue, analyzing protocols, or testing security. Packet sniffers provide this visibility by capturing raw traffic for inspection, but many are overly technical when it comes to handling binary data.
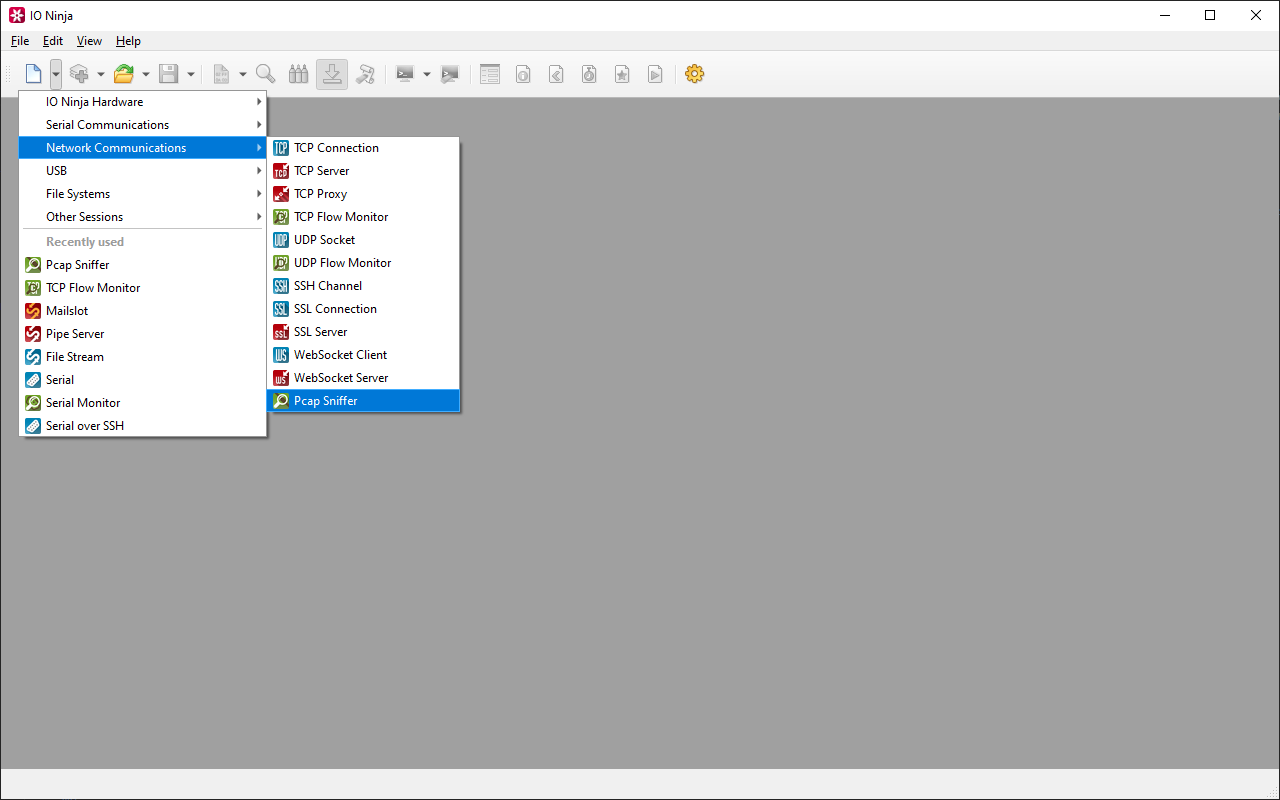
The Pcap Sniffer plugin offers a more streamlined approach. Built on the proven libpcap foundation, it combines powerful capture capabilities with a uniquely readable, binary-friendly logging interface. It also goes beyond passive sniffing by allowing you to inject custom packets for advanced testing.
Why Pcap Sniffer?
A Unified Log Sheet for Binary Clarity
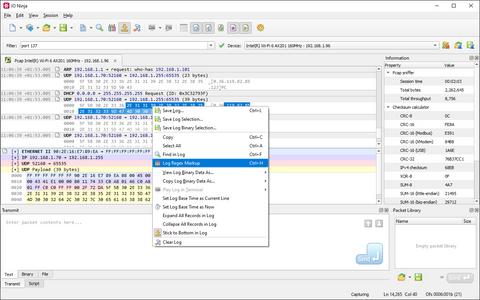
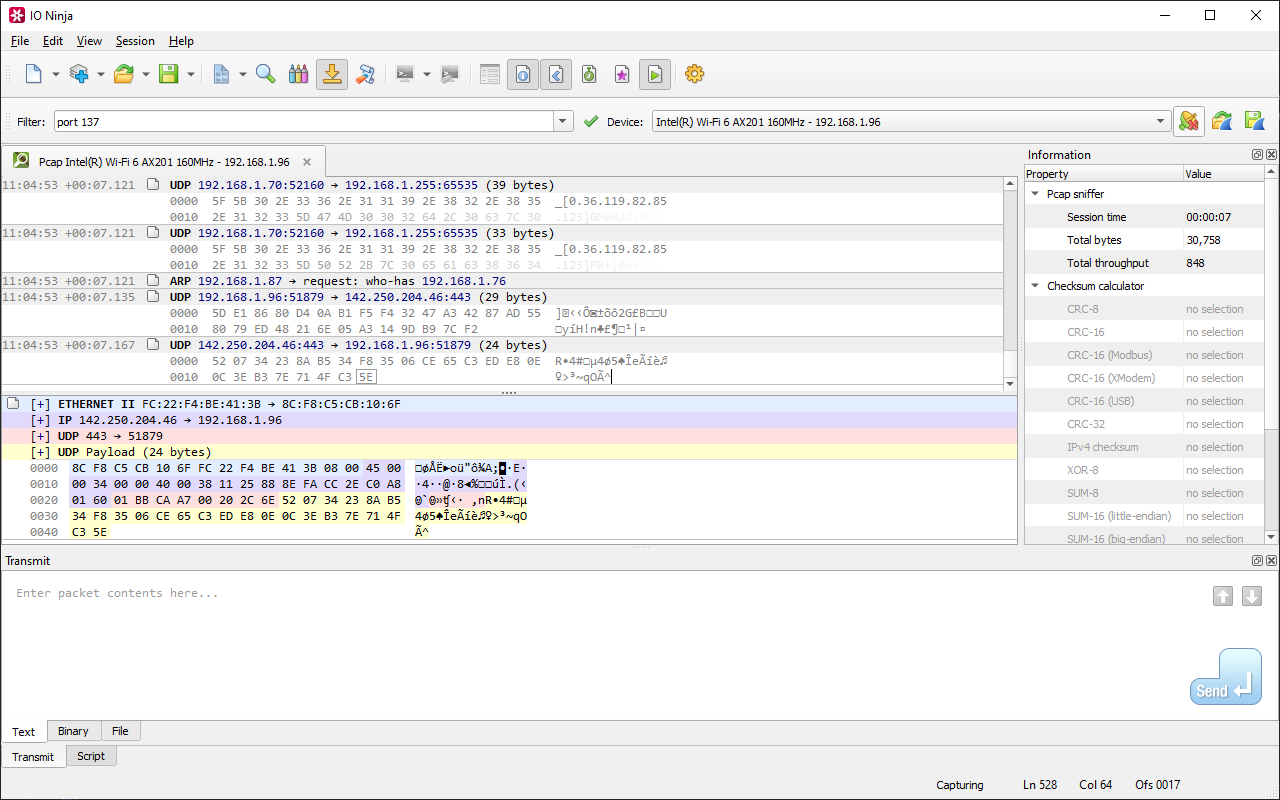
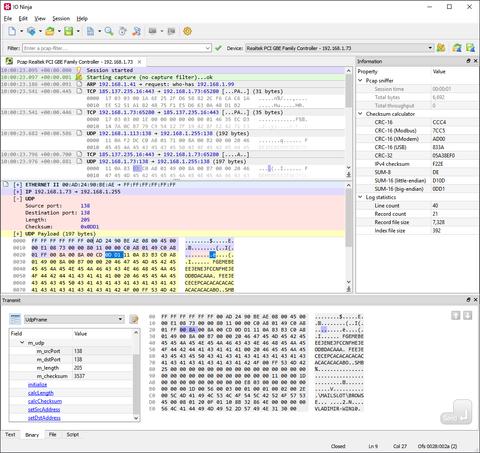
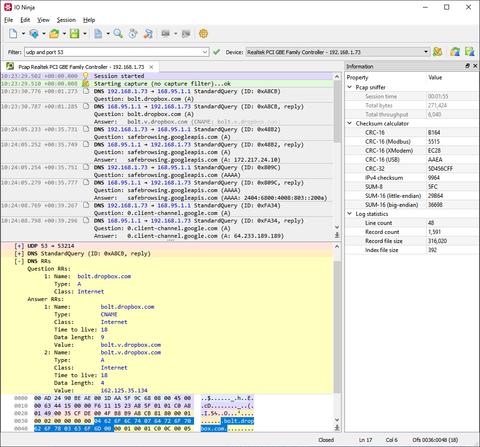
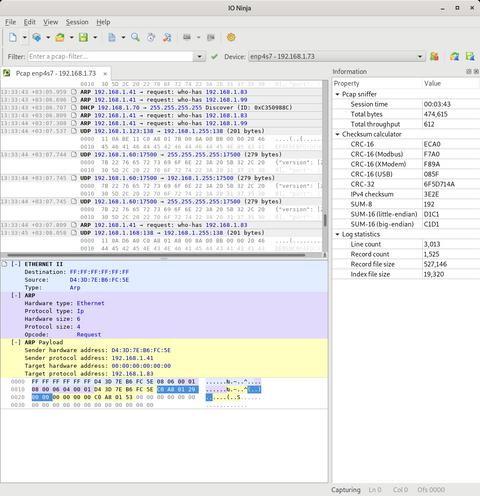
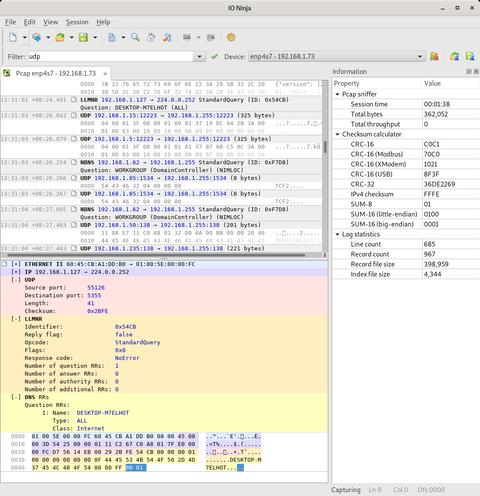
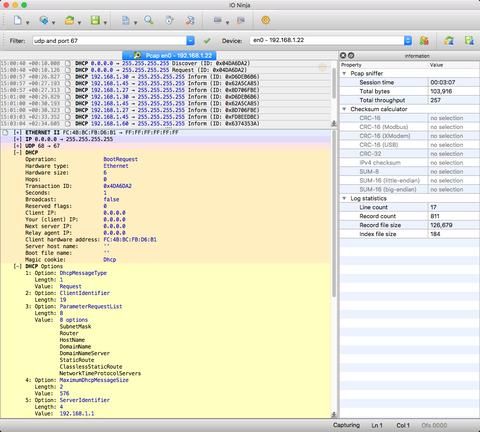
Pcap Sniffer’s standout feature is its single-view log sheet, powered by the Ninja Scroll Logging Engine. Unlike other tools that scatter information across multiple panes, this interface keeps everything: structured fields, timestamps, and raw hex, all in one continuous, readable flow. It's ideal for users who need to work directly with binary data.
More Than Just a Sniffer — It Injects Too
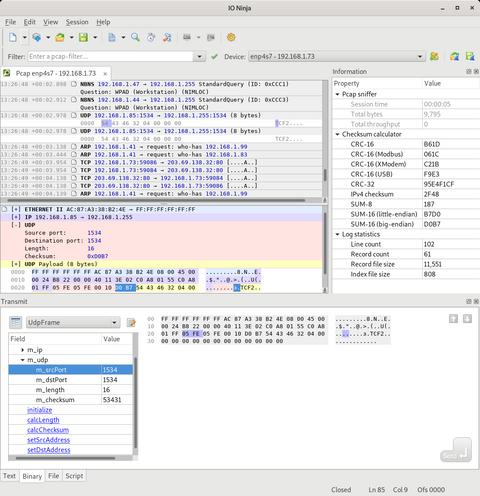
In addition to capturing packets, Pcap Sniffer enables custom packet injection. Whether you're simulating traffic, fuzzing protocols, or recreating edge-case scenarios, this feature gives you low-level control. Paired with IO Ninja’s Jancy packet template feature, it becomes a powerful tool for crafting and automating complex test cases.
Backed by libpcap
Pcap Sniffer runs on libpcap, a widely trusted packet capture library. It provides a reliable backbone for real-time monitoring, and IO Ninja builds on top with scripting, visualization, and transmission for a complete workflow.
Getting Started
Documentation
See Also
| Plugin | Relevance |
|---|---|
| A TCP Analyzer that can be attached to Pcap Sniffer. |