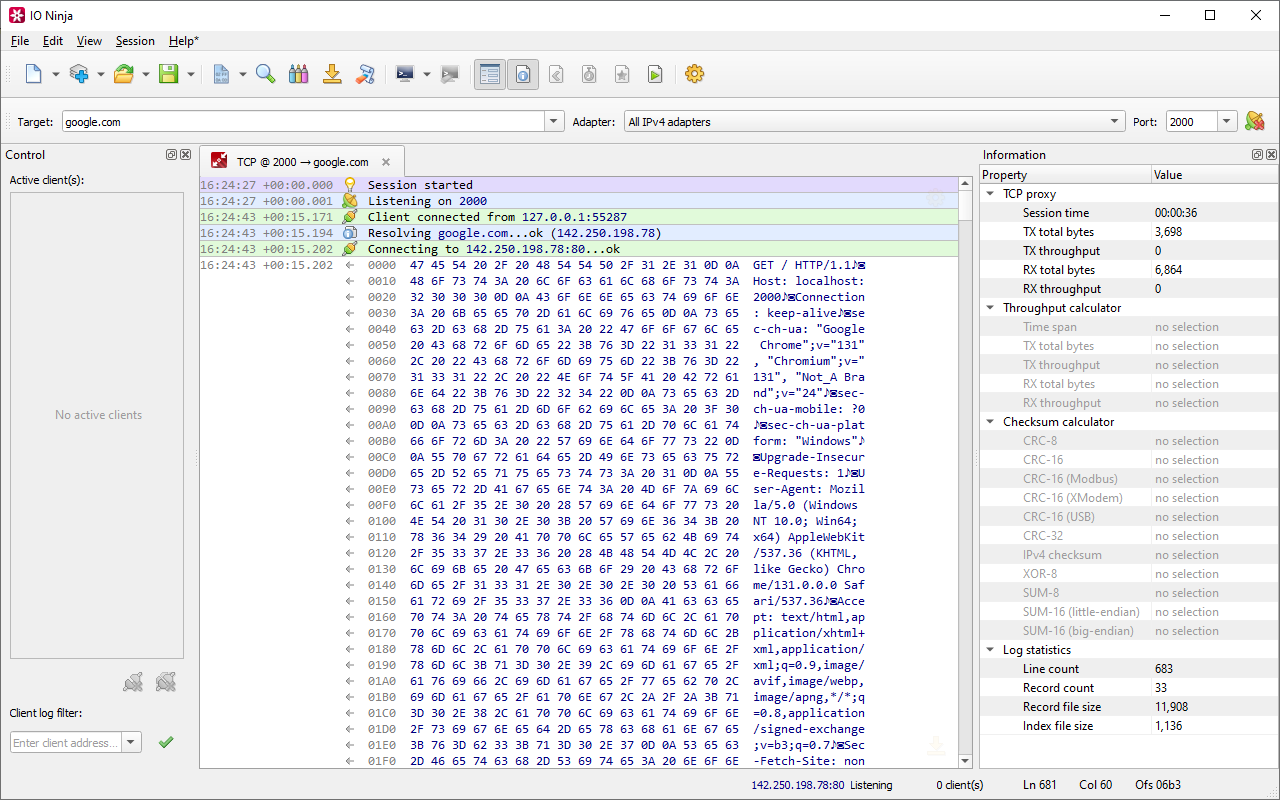
TCP Proxy
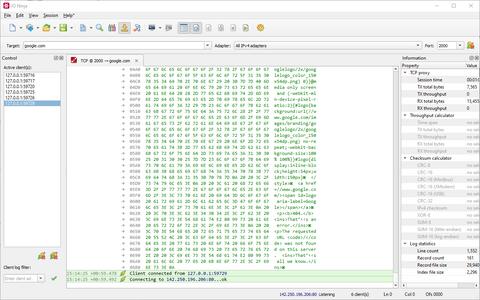
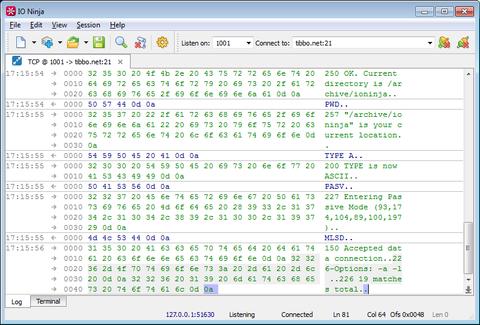
Your Man-in-the-Middle for TCP CommunicationsThe TCP Proxy plugin serves as an essential tool for inspecting data exchanged between two TCP nodes. Functioning as a man-in-the-middle, it offers a seamless way to monitor and log TCP communication, addressing common limitations encountered with traditional sniffing tools like the Pcap Sniffer plugin.
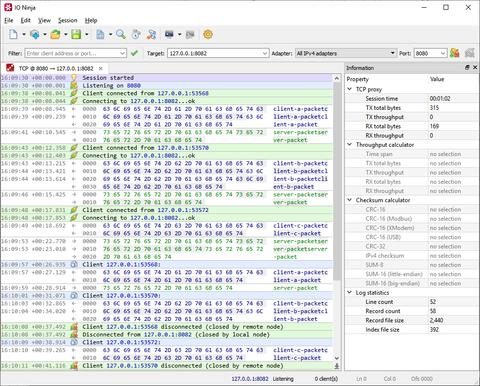
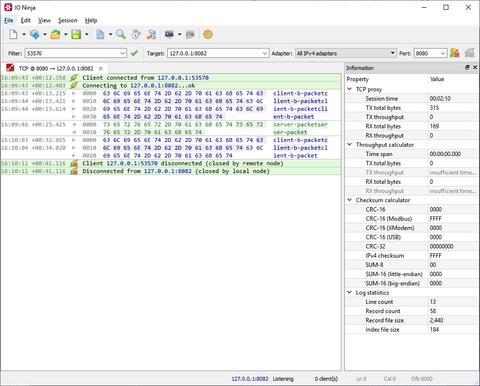
The plugin operates by setting up a local interface and TCP port for listening and a designated destination address for connection. Whenever a client connects to its server side, it establishes a secondary connection with the specified endpoint; then passes data between the client and the server while logging everything in the process.
How TCP Proxy Makes TCP Inspection Easy
Reliable Data Inspection for Any Network
Intercepting TCP packets using a sniffer often proves challenging in environments like Wi-Fi or segmented Ethernet networks. The TCP Proxy plugin addresses this by acting as a bridge, redirecting TCP communication through its controlled interface. This approach ensures that users can monitor even connections outside their immediate network segment without limitations.
Multi-Connection Handling with Filtering
The TCP Proxy plugin supports multiple simultaneous connections, enabling users to monitor extensive network activity efficiently. When the log becomes cluttered, users can apply filters to isolate and focus on specific conversations, ensuring precise data analysis without distractions.
Powerful & Beautiful Logging Engine
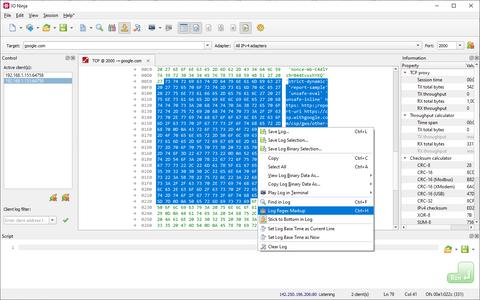
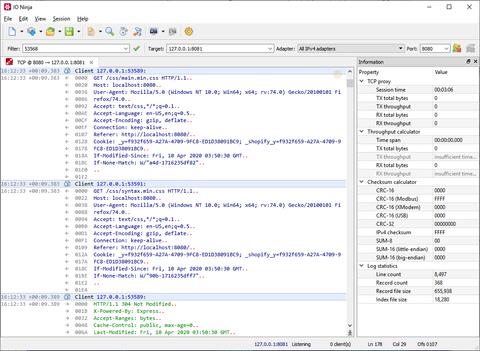
The Ninja Scroll logging engine is the heart of IO Ninja! It offers many unique and useful features you won't find in other TCP proxies, such as interleaving binary data with informational messages for a clear timeline of events, switching between hex-view and plain-text view of binary data, a regex markup engine for highlighting data based on regular expressions, and many others!
Getting Started
Documentation
See Also
| Plugin | Relevance |
|---|---|
| Connect, send and analyze TCP packets. | |
| Accept incoming TCP connections. | |
| Reconstruct TCP streams from packets captured via Pcap. |