TCP Flow Monitor
The TCP Flow Monitor plugin provides an elegant way to see just the data and nothing else. Specify an interface to capture packets on, specify a filter in the form of address (or just port) and forget about packets! You will receive a clean log of data exchange reconstructed from the captured packets behind the scene - and in real time (no capture-first-re-create-conversation-later). The end result will look just like the one you see in TCP Connection plugin or TCP Listener plugin.
Basic Setup
In IO Ninja, click the “New Session” dropdown and select “TCP Flow Monitor”.
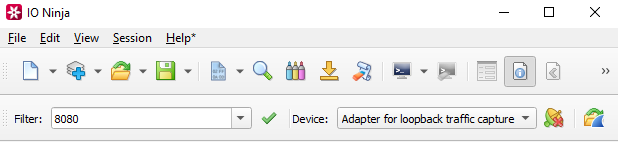
In the “Filter:” field, type a capture filter, e.g. “8080” (to capture traffic on port 8080).
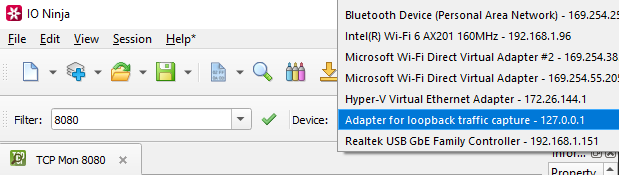
Select a network interface from “Device:”, e.g. “Adapter for loopback traffic capture”.
Click the “Capture” button to the right of the “Device:” dropdown to start capturing traffic.
Monitor TCP traffic captured according to your filter.
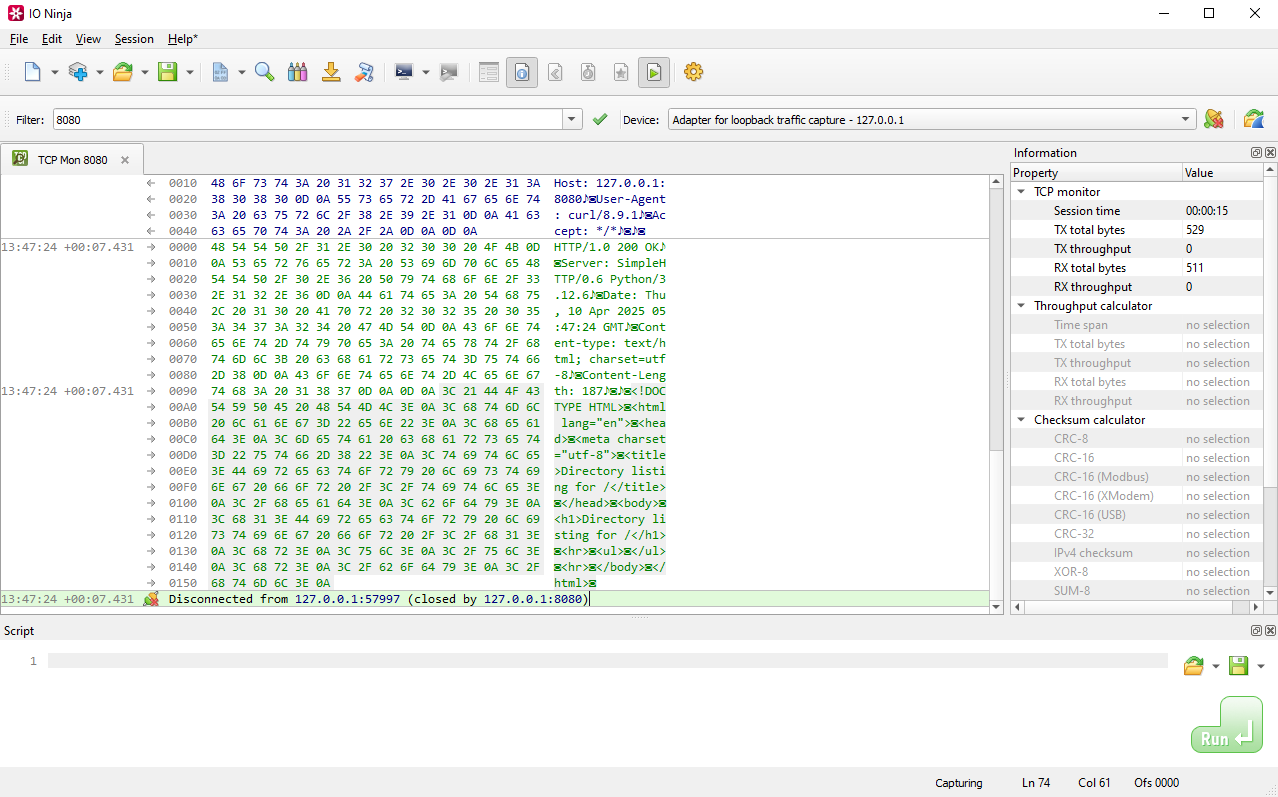
Adjust settings as needed via the “Settings” button (see “Settings” section below for details).
Settings
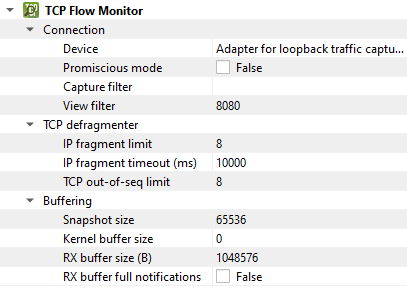
Setting |
Description |
Default |
|---|---|---|
Device |
The device to capture. |
|
Promiscious mode |
Intercept and analyze all network traffic, not just the data specifically directed to it. |
False |
Capture filter |
Term to filter with when capturing packets. Supported filters include: |
|
View filter |
Term to filter with when displaying packets. |
|
IP fragment limit |
The maximum number of IP fragments. IP fragments refer to the pieces of a larger IP packet that has been broken up for transmission across a network. IP datagrams can be fragmented during transmission, and the TCP Flow Monitor attempts to reassemble these fragments into complete packets. To do this, it maintains a database of observed fragments. However, if the network contains malformed or maliciously crafted fragments, the defragmentation process can be overwhelmed. To prevent this, the analyzer applies several sanity checks. For example, incomplete fragment chains are discarded after a timeout to avoid indefinite retention, and the number of fragments in a chain is limited—since it’s highly unlikely that a legitimate IP datagram would be split into more than a few parts. By enforcing these limits, the analyzer can effectively discard suspicious or malformed chains, making the defragmentation process more robust and secure in hostile network environments. |
8 |
IP fragment timeout (ms) |
The maximum delay between IP fragments. |
10000 |
TCP out-of-seq limit |
Maximum number of out-of-order TCP segments. |
8 |
Snapshot size |
Pcap (packet capture) snapshot size. |
65536 |
Kernel buffer size |
Pcap (packet capture) kernel buffer size. |
0 |
RX buffer size (B) |
The full size of the incoming data ( |
1048576 |
RX buffer full notifications |
Toggle warnings in log about the incoming data ( |
False |
Note
“Capture filter” filters what is captured, while “View filter” filters the log after capturing. Only use “Capture filter” if you are sure that you will not later need the packets that you are filtering out. If you may need the packets later, capture everything and filter using the “View filter”.