SSL Connection
The SSL Connection plugin turns IO Ninja into a highly configurable raw SSL client-side terminal.
Basic Setup
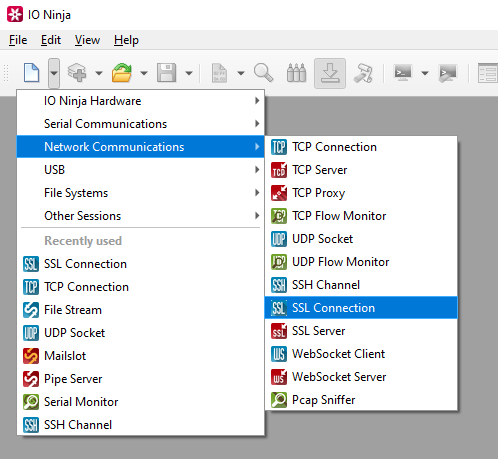
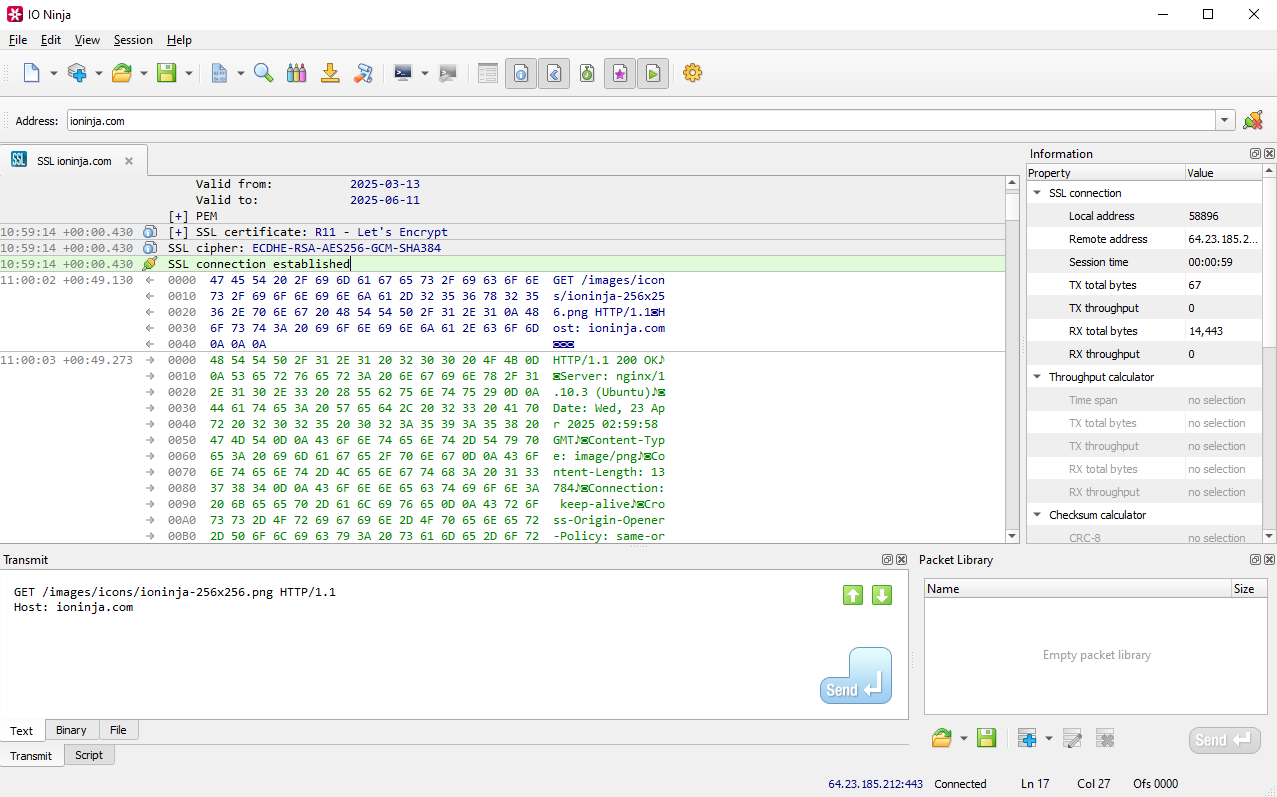
In IO Ninja, click the “New Session” dropdown and select “SSL Connection”.
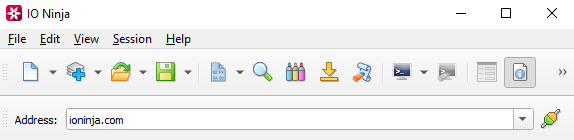
Type your remote address e.g. “ioninja.com” and click “Connect”.
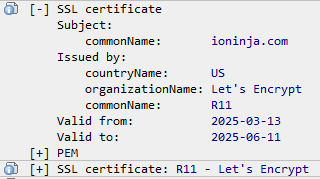
You can expand SSL certificates by pressing the [+] button, and even copy the PEM blob.
Send packets using the “Transmit” pane and see responses in the log.
Note
For basic testing, you can try to pull IO Ninja’s logo with the following GET packet:
GET /images/icons/ioninja-256x256.png HTTP/1.1
Host: ioninja.com
Remember to add two blank lines after the last header line to indicate the end of the request.
Adjust settings as needed via the “Settings” button (see “Settings” section below for details).
Settings
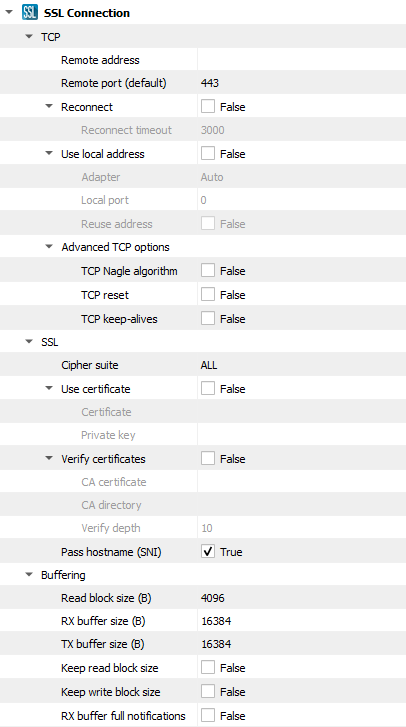
Setting |
Description |
Default |
|---|---|---|
Remote address |
Remote address to connect to. Can be specified via IPv4 ( |
|
Remote port (default) |
Remote port to connect to in cases when a port is not explicitly specified in Remote address. |
80 |
Reconnect |
Attempt to reconnect when connection is dropped by the remote node. |
False |
Reconnect timeout |
The delay between reconnect attempts. |
3000 |
Use local address |
Bind socket to the specified local address. |
False |
Adapter |
Local network adapter to bind to. Pick one from the list of installed network adapters (or bind to all installed |
Auto |
Local port |
Local port to bind to. Setting this to |
8080 |
Reuse address |
Allow multiple sockets to share the same local address. Maps to the |
False |
TCP Nagle algorithm |
Delay transmission to reduce the number of small |
False |
TCP reset |
Drop TCP connections abruptly with a |
False |
TCP keep-alives |
Detect connection loss with |
False |
Security level |
Specify OpenSSL security level. Read more about OpenSSL security levels here. |
1 |
Cipher suite |
Select an OpenSSL cipher mode. OpenSSL ciphers refer to the cryptographic algorithms supported by the OpenSSL library for securing data in transit, typically over SSL/TLS connections. Read more about OpenSSL ciphers here. See avaialble options. |
ALL |
Use certificate |
Whether or not to use a client-side certificate for the SSL connection (PEM format). |
False |
Certificate |
Specify the file path of the client-side certificate (PEM format). |
|
Private key |
Specify the private key for the client-side certificate (PEM format). |
|
Verify certificates |
Whether or not to verify the server-side certificate of the target SSL server (PEM format). |
False |
CA certificate |
Specify the file path of the server-side CA certificate to be used for verification (PEM format). |
|
CA directory |
Specify a directory of server-side CA certificates to be used for verification (PEM format). |
|
Verify depth |
Specify the maximum certificate certificate chain length. A certificate chain is a sequence of certificates—starting with the SSL/TLS certificate and followed by one or more Certificate Authority (CA) certificates—that allows the recipient to verify the authenticity and trustworthiness of both the sender and the issuing CAs. |
10 |
Pass hostname (SNI) |
Whether or not to pass the hostname during the handshake for SNI (Server Name Indication). SNI is an extension of the TLS networking protocol that enables a client to include the hostname it is trying to connect to as part of the TLS handshake process. |
True |
Read block size (B) |
The size of each individual read block submitted to the underlying transport. |
4KB |
RX buffer size (B) |
The full size of the incoming data ( |
16KB |
TX buffer size (B) |
The full size of the outbound data ( |
16KB |
Keep read block size |
Don’t merge read blocks in RX buffer. Incoming data blocks coming in quick succession can be merged together so that IO Ninja writes them to log as a whole. When this option is set to |
False |
Keep write block size |
Don’t merge write blocks in |
False |
RX buffer full notifications |
Toggle warnings in log about the incoming data ( |
False |
Cipher Suite Options
Cipher Suite |
Cipher Strings |
Description |
|---|---|---|
Encrypted |
|
All cipher suites are included except for the |
Encrypted & authenticated |
|
Refers to all cipher suites supported by OpenSSL that provide both encryption and authentication. This is achieved by including |
OpenSSL default |
|
Includes all the ciphers from the |
All (including unencrypted) |
|
Uses the |
Read more about OpenSSL ciphers here.
Note
An example of an adapter dropdown on a typical Windows laptop is shown below: