TCP Flow Analyzer
TCP Flow Analyzer is the layer version of TCP Flow Monitor. It can be attached to Pcap Sniffer or Ethernet Tap to convert low-level packet views into high-level data flow representations.
Basic Setup
In a Pcap Sniffer or Ethernet Tap session, attach the TCP Flow Analyzer layer.
Analyze Pcap Sniffer or Ethernet Tap logs as if they were TCP Proxy or TCP Server session logs.
Adjust settings as needed via the “Settings” button (see “Settings” section below for details).
Settings
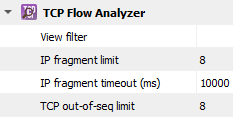
Setting |
Description |
Default |
|---|---|---|
View filter |
Term to filter with when displaying packets. Supported filters include: |
|
IP fragment limit |
The maximum number of IP fragments. IP fragments refer to the pieces of a larger IP packet that has been broken up for transmission across a network. IP datagrams can be fragmented during transmission, and the TCP Flow Analyzer attempts to reassemble these fragments into complete packets. To do this, it maintains a database of observed fragments. However, if the network contains malformed or maliciously crafted fragments, the defragmentation process can be overwhelmed. To prevent this, the analyzer applies several sanity checks. For example, incomplete fragment chains are discarded after a timeout to avoid indefinite retention, and the number of fragments in a chain is limited—since it’s highly unlikely that a legitimate IP datagram would be split into more than a few parts. By enforcing these limits, the analyzer can effectively discard suspicious or malformed chains, making the defragmentation process more robust and secure in hostile network environments. |
8 |
IP fragment timeout (ms) |
The maximum delay between IP fragments. |
10000 |
TCP out-of-seq limit |
Maximum number of out-of-order TCP segments. |
8 |