TCP Proxy
| Requires: | org.jancy.io.net org.jancy.io.server org.jancy.io.tcp |
| Optional: | org.jancy.io.ip4 org.jancy.io.ip6 |
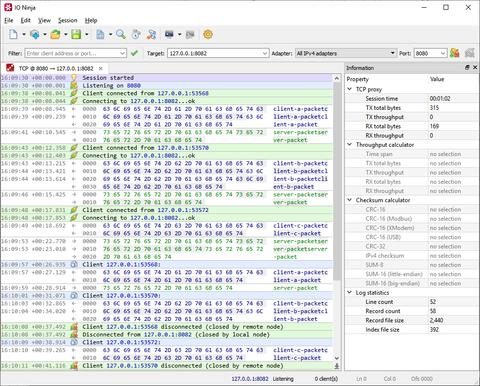
The TCP Proxy plugin is a man-in-the-middle for TCP connections. Just like the Pcap Sniffer plugin, it is intended for inspecting data being passed between 2 TCP nodes.
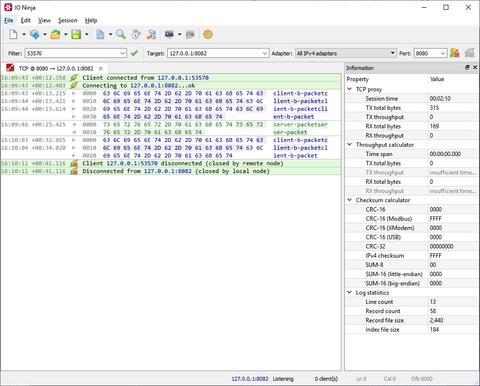
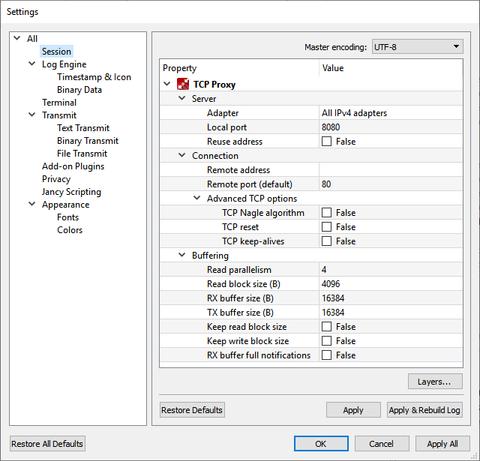
You set it up with a specific interface and a local TCP port to listen on and a specific destination address to connect to. Whenever a client connects to the server side of TCP Proxy, the client side establishes a secondary connection to the specified desintation. Then TCP Proxy keeps passing data back and forth between its two peers while logging everything in the process.
In some situations, this proxy approach is better than a sniffer.
Using a sniffer for intercepting the packets of a connection you want to monitor isn't always easy. For example, if it's TCP over Wi-Fi, Pcap may not cut it. Or it could be regular Ethernet networking, but with both nodes outside of your local network segment, beyond the reach of Pcap. Redirecting TCP communications through the TCP Proxy plugin solves these problems.
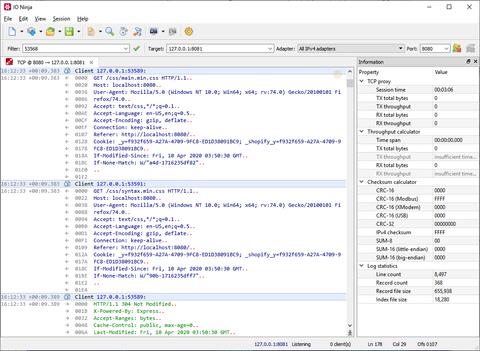
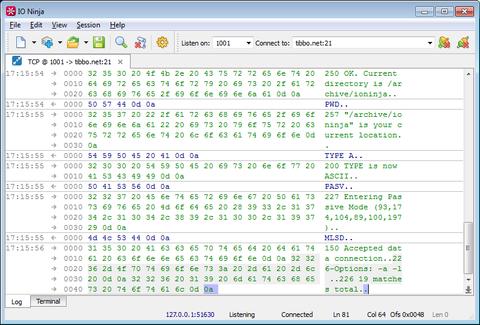
Another reason to use a proxy instead of a sniffer is clarity of representation. When you use a TCP proxy, it's easy to follow the actual data exchange. The log looks just like when you're using the TCP Connection plugin, as opposed to the packet-based representation generated by a sniffer.
The TCP Proxy plugin allows you to accept and maintain multiple incoming connections at the same time. If the log gets too messy — apply a filter and leave only the conversation with a particular client while hiding everything else.